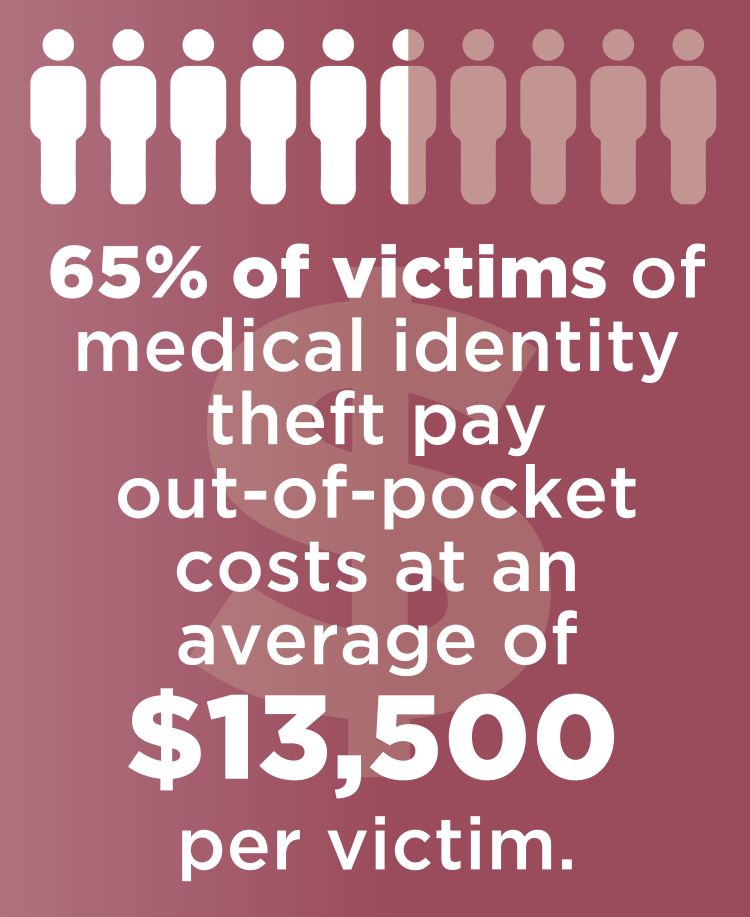
The healthcare market is lucrative. The data is extensive, sensitive and cyber criminals are poised to launch increasingly nuanced attacks in the coming years looking to manipulate information stored across the world on smart-connected health devices and hospital systems.
Combating future attacks like 2017’s massive WannaCry ransomware and NotPetya malware incidents will require improved cooperation among all international healthcare stakeholders, an effort Philips Healthcare is poised to lead. With its early adoption of mandatory vulnerability disclosure protocols and ongoing drive to be the first major company to require a software bill of materials for its healthcare products, Philips is well positioned to lead the global security conversation and foster an improved information sharing environment.
Michael McNeil, Philips head of global product and security services, calls a cooperative approach to cyber protection the critical component to deterring malicious actors and responding to growing threats. “I believe it’s very critical to be transparent and open as an organization. It’s important to help coalesce and bring all of the stakeholders together around the topic,” McNeil said. “We’re really focused on the thought leadership aspect. That’s the external piece we want to drive. There are certain elements that Philips can lead in improving the area of threat information sharing.”

Driving Philips' role as a leader in healthcare cybersecurity protection is their commitment to instituting policies that foster transparency with consumers and to building in practices that get out in front of threats before products or health systems are compromised. Back in 2014, Philips was the first medical device company to stand up a full vulnerability disclosure policy process. Officials instituted the protocol two years before it was mandated by the Food & Drug Administration (FDA) in 2016.
“We made it very transparent that if you identify vulnerabilities in our solution set, whether that’s our baby monitors or toothbrushes that are connected to the internet or an ultrasound device, we have an open door policy to provide you with the secure mechanisms to communicate with us,” McNeil said. “And then we work together on the delivery of a more secure solution.”
McNeil acknowledges that software vulnerabilities are an unfortunate inevitability with cyber criminals always on the hunt for a new avenue for exploitation.
Philips’ policy allows consumers to easily report flaws. In turn, the company’s cyber technicians can rapidly patch known issues and ensure future systems are as secure as possible.

“We recognized that policy as a major element of execution, and it allowed us to make sure that we were leading in this area in the marketplace,” McNeil said.
A February 2018 white paper from Philips discusses the complex privacy and technical concerns associated with healthcare cybersecurity and acts as an extension of the company’s transparency policy. The report discusses the latest challenges in defending health systems and the expected trends healthcare providers can expect in the near term.
Taking a forward-looking approach, Philips officials are readying a new policy requiring a “software bill of materials” to be included on all internet-connected smart health devices.
“Philips has been very proactive in updating our documentation to be able to provide that software bill of materials to customers upon their request,” McNeil said.
McNeil compared the policy, which is being actively discussed by the FDA, to a nutrition label on food packaging where particular software specifics would be noted so operators can be fully aware of how to best protect the device.

Just as WannaCry and NotPetya spread across borders and attempted to infiltrate health systems across the world, future cyberattacks are expected to be perpetrated from anywhere to anywhere. Philips’ position as a global company works in its favor as an international partner to quickly share information on threats and rapidly respond to attacks.
“Cyber is a global attack vector. The Petra Meltdown activity started in the U.K., and then spread globally. WannaCry’s malware could try and cripple a system in any geography. It becomes very critical when you as an organization, and Philips specifically, are aligned with a number of global regulatory bodies and security sharing organizations,” McNeil said. “We have associates aligned across the globe to give us the ability to execute in a much more proactive way by having that broad view and landscape that we focus on.”
That partnership extends to the engaged role Philips has with U.S. regulatory and standards bodies in helping to shape cybersecurity policy efforts to best protect consumers.

“We are also very highly active and involved in industry and government forums. One of those was the recent participation in a Department of Health and Human Services cybersecurity task force, where Philips directly developed recommendations to the legislature.”
McNeil works directly with the FDA, the Medical Imaging & Technology Alliance, the International Organization for Standardization (ISO), and has testified before Congress to inform legislative action.
The FDA plans to include a note in its imminent Medical Device Safety Action Plan calling on Congress to update pre-market guidance for device manufacturers to adhere to enhanced security protocols.
Philips’ work leading this effort to bring healthcare stakeholders together will only become more imperative as cyber actors continue to develop more sophisticated methods of infiltrating systems.
“When someone asks ‘what keeps you up at night?’ Well, for me, the very first thing is any ability to compromise the functionality and the information coming from the products Philips sells in the marketplace,” McNeil said.
McNeil noted that cyber actors are increasingly working to get access to data and manipulate to either disrupt functions or hold the information for ransom. The most immediate goal is to ensure Philips’ health products have resilient cyber functions so they can’t be used as a backdoor to take hold of data on hospital systems.
“Acquiring data and using it for financial gains, yes, that is something that is major. The data itself is something that’s considered to be at a premium compared to someone just getting your credit card,” McNeil said. “It’s more critical if someone says they’re going to take this health information and they’re going to use it to compromise your environment, so that it shuts down your operations and your ability to render appropriate services and hold your institutions hostage.”

In coordination with its external efforts to lead policy discussion on international standards, Philips also continues to work on testing all of its devices, enacting appropriate protocols to ensure security, creating frameworks based on industry best practices and running full risk assessments.
“You have to understand the customers, the marketplace, the FDA, the regulators. It’s important to know what their expectations are and what needs to be improved within the system itself. We have a number of policies and controls that we use to test our products and assess them before launching them into the marketplace,” McNeil said.
Internet-connected smart devices have revolutionized consumers’ ability to track data and optimize their health activity, and McNeil wants to ensure users that their products remain safe through their entire lifecycle.
“As products and solutions are being done, we have to reinforce in those environments appropriate mitigating and compensating controls. That includes making sure that the solution itself that may have certain vulnerabilities now has firewalls. Or it could be Philips doing the appropriate testing and threat monitoring,” McNeil said.
Ultimately, McNeil recognizes that Philips efforts will be best optimized in a collective approach that brings all stakeholders together to continue working on a cyber problem that evolves by the day.
“This can’t be solved by just one organization. It has to be something that all of the major players are able to impact,” McNeil said. “We want to, as a community, tackle and deal with improving the complexity of cyberspace.”